After many years of evolution, ransomware has emerged as one of the most troublesome malware categories of our time. The threat is known for locking computers or encrypting files to trick users into handing over their money. Ransomware has had a global spread as, according to Symantec’s telemetry, 11 of the top 12 countries impacted by ransomware in the past 12 months are all direct or indirect member states of the G20 organization. India ranks as the 9th most impacted region by ransomware with other countries like US, Japan, the UK, Italy and Germany topping the charts.
With the increasing spread of connected devices, such as wearable computers and the Internet of Things (IoT), ransomware may be on the cusp of another evolutionary jump forward. In its latest research, Symantec learned that it would not be difficult for current-generation ransomware to make the leap from mobile phones to wearable devices such as smartwatches. While Google first introduced the Android Wear smartwatch OS to the public in early 2014, the recent arrival of the Apple Watch has given this sector a significant boost. This is creating a fledgling market for smartwatch apps which developers have started to cater to.
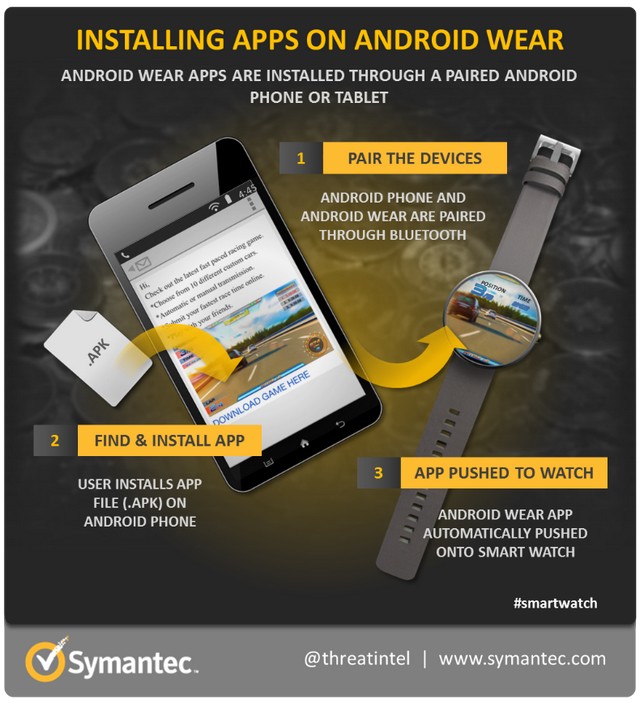
Android Wear devices are designed to be paired with a more function-rich device such as an Android phone or tablet. The OS allows existing Android apps to use certain features of the Android Wear device with no extra work. But if developers want to really take advantage of the features in the smaller wearable devices, they can write apps specifically for it.
The process of installing an Android Wear app is designed to be a seamless experience. If an installed Android mobile app has an Android Wear component or if it was created for Android Wear, the app will automatically be pushed from the mobile device onto the Android Wear smartwatch.
Given that there are already ransomware threats in circulation for Android mobile devices, Symantec tested how an Android Wear device might be impacted by typical Android ransomware. To do this test, they simply had to repackage a current Android ransomware .apk file – Android.Simplocker – inside a new Android Wear project to create a new .apk file.
Next, researchers at Symantec took a Moto 360 smartwatch and paired it with an Android phone. When they installed the new .apk file on the phone, they found that the phone became infected with the ransomware as expected. As the smartwatch was paired with the phone, the ransomware was also pushed onto the smartwatch. Once installed on the smartwatch, the malware could be executed by the user if they were tricked into running it, thinking it was a useful app.
After the ransomware was executed, it caused the smartwatch to become generally unusable. Simplocker has a routine that checks for the display of the ransom message every second, and if it is not shown, it will push it onto the screen again. This activity prevented them from using the device. Simplocker also encrypted a range of different files stored on the smartwatch’s SD card.
So far, Symantec has not seen any ransomware in the wild specifically designed to target smartwatches but this situation could easily change. This scenario could give rise to the term “ransomwear”—ransomware that you can wear.


)



