Design in user experience is important to maintain the consumer’s interaction with an interface; be it a software or a website. Just as much as we are concerned with security at a public place such as an airport, we need to be equally concerned with security while transacting on a digital platform such as a mobile application. Although designers are not typically responsible for technical priorities on an operational level, the goal is to perform a balancing act that can bring level to both sophistication and simplicity. [caption id=“attachment_4193123” align=“alignleft” width=“380”]
 Anupam Kulkarni, Co-Founder of iauro Systems[/caption] But as Leonardo da Vinci once said, ‘simplicity is the ultimate sophistication’. Security is, after all, not uncommonly an afterthought in product development. So, does security bring the sophistication to simplicity? As difficult as it is to design a security protocol while considering UX design, it is just as difficult to design a user experience, while considering security protocols. User experience and security has been closely studied academically and is known as HCISec (also referred to as HCI-SEC or Human Computer Interaction and Security). Security professionals give utmost priority to system security. In this sense, security revolves around the digital identity with sensitive information that is attached to that identity. They must ascertain that only authorized users have access to the framework and ensure that users are safe in the knowledge that their information is safe online. Further to that, a user can be under full protection only if the app knows who it is protecting. When we come to a stage where a personal piece of data like a phone number is required, it strengthens the digital identity of the user the app. The app will then record it once and never need the user to go through the trouble of entering it again. [caption id=“attachment_4193109” align=“alignnone” width=“825”]
Anupam Kulkarni, Co-Founder of iauro Systems[/caption] But as Leonardo da Vinci once said, ‘simplicity is the ultimate sophistication’. Security is, after all, not uncommonly an afterthought in product development. So, does security bring the sophistication to simplicity? As difficult as it is to design a security protocol while considering UX design, it is just as difficult to design a user experience, while considering security protocols. User experience and security has been closely studied academically and is known as HCISec (also referred to as HCI-SEC or Human Computer Interaction and Security). Security professionals give utmost priority to system security. In this sense, security revolves around the digital identity with sensitive information that is attached to that identity. They must ascertain that only authorized users have access to the framework and ensure that users are safe in the knowledge that their information is safe online. Further to that, a user can be under full protection only if the app knows who it is protecting. When we come to a stage where a personal piece of data like a phone number is required, it strengthens the digital identity of the user the app. The app will then record it once and never need the user to go through the trouble of entering it again. [caption id=“attachment_4193109” align=“alignnone” width=“825”]
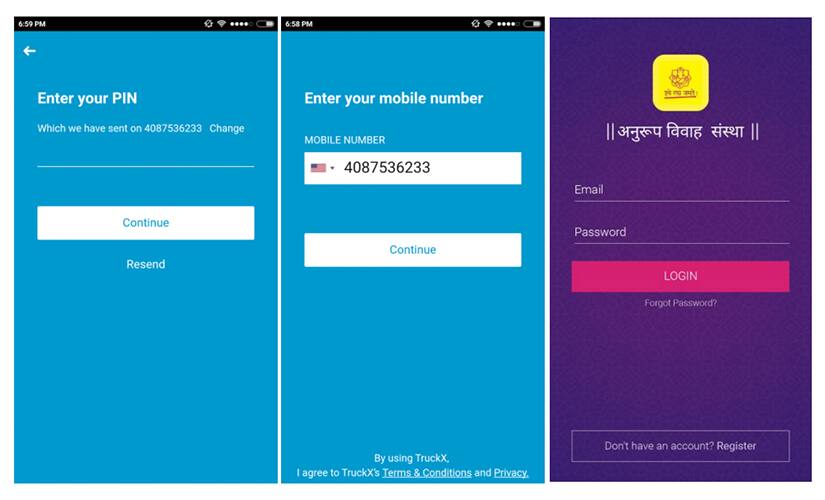 UX for TruckX and Anuroop Matrimony[/caption] Similarly, granting an app permission to user data is important for the best mobile experience. Certain algorythyms are computated and connected to the user. For instance when location of a user is stored, it is assimilated by the app to facilitate a mobile experience that depending on the requirement. [caption id=“attachment_4193111” align=“alignleft” width=“380”]
UX for TruckX and Anuroop Matrimony[/caption] Similarly, granting an app permission to user data is important for the best mobile experience. Certain algorythyms are computated and connected to the user. For instance when location of a user is stored, it is assimilated by the app to facilitate a mobile experience that depending on the requirement. [caption id=“attachment_4193111” align=“alignleft” width=“380”]
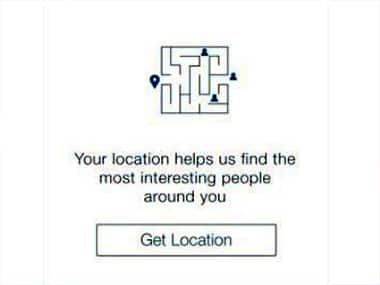 Location Permissions improves user experience[/caption] It is important to keep in mind that a user is involved in the decision making processes, while trafficking a digital interface. It is their involvement to interact, utilize or transact. Hence, the importance to facilitate trust amongst your users is important in addtion to engaging consumers in seamless user experience. For example, the green lock at the top of an internet browsers address bar satisfies many users. It is more or less like a game of passing the baton between the bouncer and the entertainer at a club. Similarly, the fingerprint scanner that mobile phones have recently incorporated has inculcated a feeling of absolute security, since only the person with the unique fingerprint can access the next step. Fingerprint scanners are the next stage of validating a digital identity. Every single moment of interaction that helps a user flow through a UX structure is considered a microservice. Users want water-tight secure network to share their personal information on. This explains why a password is asked to be 5 or 8 characters. Time is spent on the minute details. What provides essential flow to a security protocol, in this respect, is complemented with graphics that one can identify with. Considering the security and user experience debate, the primary concern of UX designers and security technicians lie in two perspectives:
Location Permissions improves user experience[/caption] It is important to keep in mind that a user is involved in the decision making processes, while trafficking a digital interface. It is their involvement to interact, utilize or transact. Hence, the importance to facilitate trust amongst your users is important in addtion to engaging consumers in seamless user experience. For example, the green lock at the top of an internet browsers address bar satisfies many users. It is more or less like a game of passing the baton between the bouncer and the entertainer at a club. Similarly, the fingerprint scanner that mobile phones have recently incorporated has inculcated a feeling of absolute security, since only the person with the unique fingerprint can access the next step. Fingerprint scanners are the next stage of validating a digital identity. Every single moment of interaction that helps a user flow through a UX structure is considered a microservice. Users want water-tight secure network to share their personal information on. This explains why a password is asked to be 5 or 8 characters. Time is spent on the minute details. What provides essential flow to a security protocol, in this respect, is complemented with graphics that one can identify with. Considering the security and user experience debate, the primary concern of UX designers and security technicians lie in two perspectives:
- How do UX experts fit security in their digital representation
- How do security experts fit speed and comfort in their agenda
[caption id=“attachment_4193113” align=“alignnone” width=“825”]
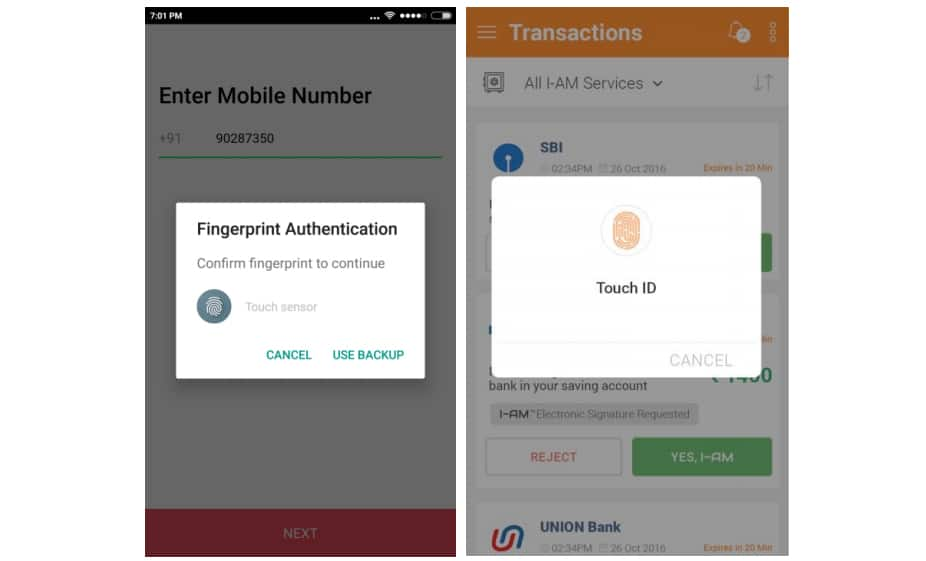 Fingerprint Authentication designed for I-AM App and Paw Santa[/caption] At the end of the day, UX designers are increasingly being versed with the current world problems and adapting to various feedback with the help of data and trade-offs with users. The traditional approach of requiring a password to log in to check your email can seem cluttered for users with all those CAPTCHA codes, but simultaneously give a sense of security. As data security finds itself on the list one of the most critical issues in today’s data driven world, engagement may not be the only criteria of developing a fantastic user experience, but the degrees of freedom (read: security protocols) contribute just as much to make the experience memorable as well a trusted. The author is the Co-Founder & Director of iAuro Systems, a technology company committed to hand-holding brands on their digital transformation journey.
Fingerprint Authentication designed for I-AM App and Paw Santa[/caption] At the end of the day, UX designers are increasingly being versed with the current world problems and adapting to various feedback with the help of data and trade-offs with users. The traditional approach of requiring a password to log in to check your email can seem cluttered for users with all those CAPTCHA codes, but simultaneously give a sense of security. As data security finds itself on the list one of the most critical issues in today’s data driven world, engagement may not be the only criteria of developing a fantastic user experience, but the degrees of freedom (read: security protocols) contribute just as much to make the experience memorable as well a trusted. The author is the Co-Founder & Director of iAuro Systems, a technology company committed to hand-holding brands on their digital transformation journey.
)