Apple has been recognised in the world, as a tech company with a focus on usability. Only this time it looks like Apple has compromised on security heavily when it comes to convinience. In a report on a blog of Elcomsoft, it has been uncovered just how fragile the Apple mobile ecosystem has become after the introduction of iOS 11
. [caption id=“attachment_4238421” align=“alignleft” width=“380”] iOS 11 on iPad an iPhone. Apple[/caption] A number of changes made by the Cupertino-based tech giant in its latest software update has resulted in an authentication system that has been stripped down of essential security mechanisms. According to the report, now if a person wants to steal all your data linked to your Apple ID or iCloud account, all they have to do is find out your iPhone’s passcode. Yeah, that’s it. Your iTunes backup (where you back up all your encrypted iPhone data) which is password protected, can now be accessed using only the iPhone’s security code. If you have that code just open the iPhone and just go to Settings > General > Reset > Reset all settings. Viola. All backup passwords removed. Now you can extract information from the original user’s iPhone back up, including things such as passwords, credit card numbers, photos, videos and much more at a leisurely pace. The report also claims one can also access the original users Gmail account. Now you have the users location data, Chrome password auto-fills, Google photos and… you get the picture right? Not a pretty one by any means. This is the just the tip of the iceberg. Apparently, your Apple ID is not as safe as you thought it once was. You would think that, by common logic, changing one’s previous password would definitely require you to type in your old password. Right? Wrong. The brilliance (stupidity) of Apple is quite uncanny. If you have two-factor authentication enabled then you can actually reset your AppleID password if you know the iPhone’s security code. No user authentication. No old AppleID password. Just the iPhone’s security code. If a person can access your AppleID, then they can:
iOS 11 on iPad an iPhone. Apple[/caption] A number of changes made by the Cupertino-based tech giant in its latest software update has resulted in an authentication system that has been stripped down of essential security mechanisms. According to the report, now if a person wants to steal all your data linked to your Apple ID or iCloud account, all they have to do is find out your iPhone’s passcode. Yeah, that’s it. Your iTunes backup (where you back up all your encrypted iPhone data) which is password protected, can now be accessed using only the iPhone’s security code. If you have that code just open the iPhone and just go to Settings > General > Reset > Reset all settings. Viola. All backup passwords removed. Now you can extract information from the original user’s iPhone back up, including things such as passwords, credit card numbers, photos, videos and much more at a leisurely pace. The report also claims one can also access the original users Gmail account. Now you have the users location data, Chrome password auto-fills, Google photos and… you get the picture right? Not a pretty one by any means. This is the just the tip of the iceberg. Apparently, your Apple ID is not as safe as you thought it once was. You would think that, by common logic, changing one’s previous password would definitely require you to type in your old password. Right? Wrong. The brilliance (stupidity) of Apple is quite uncanny. If you have two-factor authentication enabled then you can actually reset your AppleID password if you know the iPhone’s security code. No user authentication. No old AppleID password. Just the iPhone’s security code. If a person can access your AppleID, then they can:
- Control your iCloud lock.
- Erase your photos and videos of any devices uploaded to the iCloud account
- Physically locate all your Apple devices connected to the account and remotely lock them or erase them.
- Remove the person’s trusted number so that you get the 2FA codes to your own SIM card.
- Access your call logs and synced data via the iCloud account
- Access your current passwords via iCloud Chain
[caption id=“attachment_4238417” align=“alignnone” width=“700”]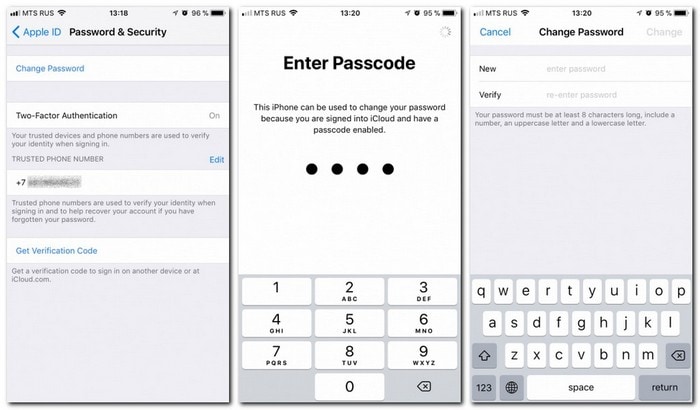 How to change AppleID password with just phone passcode. Elcomsoft blog[/caption] In short, it’s an unmitigated disaster. How Apple could have allowed such a big security loophole is anyone’s guess. You relinquish your iPhone passcode and you have just lost everything remotely connected to your Apple account. Apple’s earlier security mechanisms, as explained by the report, were the perfect balance of secure and easy. The
FBI hounding
Apple for not being able to open the Texas Church mass-shooter’s locked iPhone may have contributed to Apple dumbing down its security features. What can you do now? Well, nothing much actually other than perhaps making your iPhone passcode is 6 digits long. Let’s hope Apple can reverse these flaws in the next iOS update. For a more detailed understanding of this iOS 11 security vulnerability and how they can be exploited check out the full blog post
here
.
How to change AppleID password with just phone passcode. Elcomsoft blog[/caption] In short, it’s an unmitigated disaster. How Apple could have allowed such a big security loophole is anyone’s guess. You relinquish your iPhone passcode and you have just lost everything remotely connected to your Apple account. Apple’s earlier security mechanisms, as explained by the report, were the perfect balance of secure and easy. The
FBI hounding
Apple for not being able to open the Texas Church mass-shooter’s locked iPhone may have contributed to Apple dumbing down its security features. What can you do now? Well, nothing much actually other than perhaps making your iPhone passcode is 6 digits long. Let’s hope Apple can reverse these flaws in the next iOS update. For a more detailed understanding of this iOS 11 security vulnerability and how they can be exploited check out the full blog post
here
.
)