Researchers have discovered a new malware ‘Rombertik’ that has “multiple layers of obfuscation and anti-analysis functionality.” This functionality was designed to evade both static and dynamic analysis tools, make debugging difficult. “Security researchers are constantly looking for ways to better detect and evade each other. As researchers have become more adept and efficient at malware analysis, malware authors have made an effort to build more evasive samples. Better static, dynamic, and automated analysis tools have made it more difficult for attackers to remain undetected. As a result, attackers have been forced to find methods to evade these tools and complicate both static and dynamic analysis,” Ben Baker and Alex Chiu from Cisco Systems’ Talos Group said in a blog post. The Romberik is a complex piece of malware that is designed to hook into the user’s browser to read credentials and other sensitive information for exfiltration to an attacker controlled server, similar to Dyre. However, unlike Dyre which was designed to target banking information, Rombertik collects information from all websites in an indiscriminate manner, the blog post added. Rombertik has been identified to propagate via spam and phishing messages sent to would-be victims. Like previous spam and phishing campaigns Talos has discussed, attackers use social engineering tactics to entice users to download, unzip, and open the attachments that ultimately result in the user’s compromise. [caption id=“attachment_2230852” align=“alignnone” width=“550”] 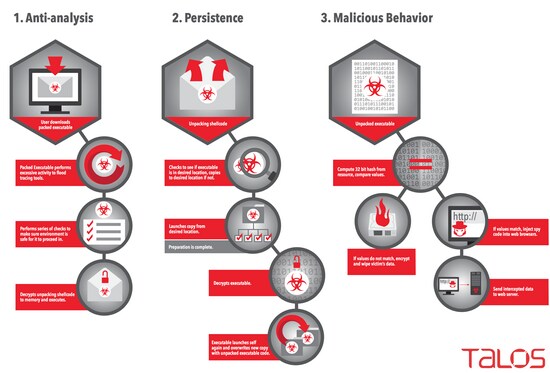 Cisco: An illustration of the step-by-step process Rombertik follows to compromise the target system.[/caption] The attackers attempt to convince the user to check the attached documents to see if their business aligns with the target user’s organisation. If the user downloads and unzips the file, the user then sees a file that looks like a document thumbnail. While this file may appears to be some sort of PDF from the icon or thumbnail, the file actually is a .SCR screensaver executable file that contains Rombertik. Once the user double clicks to open the file, Rombertik will begin the process of compromising the system, the researchers claimed. Baker and Chiu further said that the process by which Rombertik compromises the target system is a fairly complex with anti-analysis checks in place to prevent static and dynamic analysis. Upon execution, the malware will stall and then run through a first set of anti-analysis checks to see if it is running within a sandbox. Once these checks are complete, Rombertik will proceed to decrypt and install itself on the victims computer to maintain persistence. After installation, it will then launch a second copy of itself and overwrite the second copy with the malware’s core functionality. Before Rombertik begins the process of spying on users, Rombertik will perform once last check to ensure it is not being analysed in memory. If this check fails, Rombertik will attempt to destroy the Master Boot Record and restart the computer to render it unusable. The researchers found that Rombertik uses “garbage code” to inflate the volume of code an analyst might have to review and analyse. In addition, the malware stalls in sandboxes by writing a byte of random data to memory 960 million times. “If an analysis tool attempted to log all of the 960 million write instructions, the log would grow to over 100 gigabytes. Even if the analysis environment was capable of handling a log that large, it would take over 25 minutes just to write that much data to a typical hard drive. This complicates analysis.” Effectively, Rombertik begins to behave like a wiper malware sample, trashing the user’s computer if it detects it’s being analysed, according to the Talos team. “While Talos has observed anti-analysis and anti-debugging techniques in malware samples in the past, Rombertik is unique in that it actively attempts to destroy the computer if it detects certain attributes associated with malware analysis.” Good security practices, such as making sure anti-virus software is installed and kept up-to-date, not clicking on attachments from unknown senders, and ensuring robust security policies are in place for email (such as blocking certain attachment types) can go a long way when it comes to protecting users, the researchers said. However, a defense in depth approach that covers the entire attack continuum can help identify malware and assist in remediation in the event that an attacker finds a way to evade detection initially.
The Romberik is a complex piece of malware that is designed to hook into the user’s browser to read credentials and other sensitive information for exfiltration to an attacker controlled server, similar to Dyre.
Advertisement
End of Article


)

)
)
)
)
)
)
)
)



