Researchers at Malwarebytes have detected a malvertising campaign that abused several major ad networks and ran mostly uninterrupted for almost three weeks. “The threat actors responsible for this attack devised a cunning plan to pose as legitimate advertisers and employed stealthy and advanced techniques to hide malicious traffic redirections so well that they evaded most detection systems,” Jérôme Segura from Malwarebytes said in a
blogpost
. “The ultimate goal of this plan was to compromise the computers of millions of users browsing popular websites by covertly redirecting their browsers to the Angler Exploit Kit, the most advanced tool used in drive-by download attacks,” he added. [caption id=“attachment_2434544” align=“alignleft” width=“400”]
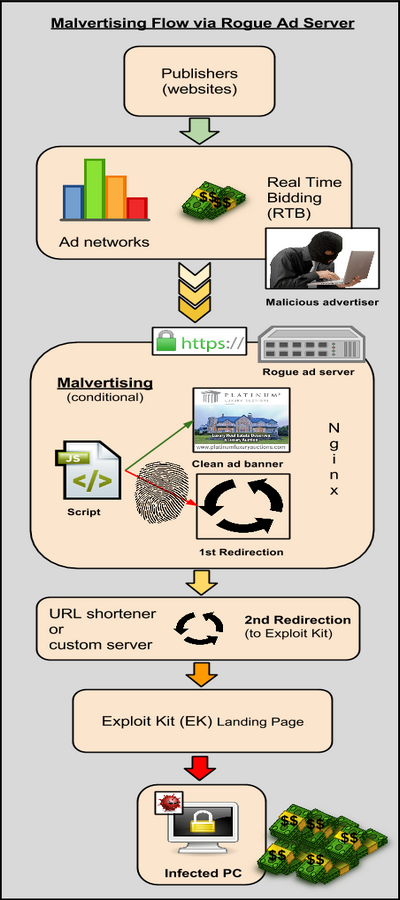
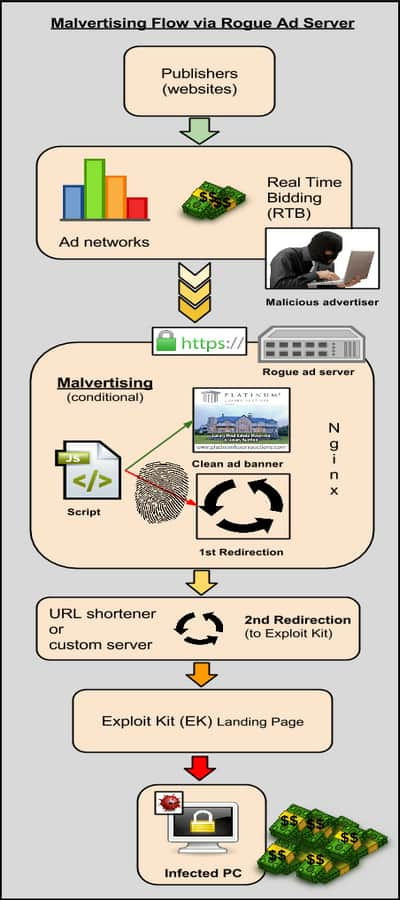 malwarebytes[/caption] Malicious actors registered to various ad platforms posing as legitimate advertisers and submitted their creatives through Real Time Bidding. The companies they were purporting to represent appeared legitimate on the surface, with websites registered years ago with even some listed in the Better Business Bureau registry. This decoy worked well enough to fool many ad networks with direct ties to the major ones in the online ad industry, the researcher stated. “The ads themselves were loaded directly from the rogue advertisers’ websites, which, as we will see it later, was part of the problem in compromising the advertising chain. However it is worth mentioning that the ads themselves were not booby trapped at all, which again made it more difficult to spot something suspicious.” The most notable publishers that were affected include: eBay.co.uk, Answers.com, Legacy.com among others. For this particular malvertising campaign, the techniques used are similar to previous ones, but great care was put on masquerading as legitimate advertisers and avoiding detection by encrypting traffic and using various advanced tricks. Use of URL shorteners, as well as a custom API to perform the redirection to the Exploit Kit landing pages were also noticed. As was the case with past malvertising attacks, the Angler Exploit Kit was used to convert incoming web traffic into infected machines. While malvertising has made headlines during the past few months, the attacks that are documented publicly are only the tip of the iceberg. There are some campaigns that are so advanced that no one will ever see or hear about them, which is exactly what threat actors are hoping for. This particular case is a good illustration of why screening advertisers is so important, especially when they are allowed to host and serve the ad content themselves. The ad could be clean or booby trapped, but the rogue actors are in full control of the delivery platform and can instruct it to perform nefarious actions that will easily bypass most security checks. Malwarebytes said that ad networks have been informed about the attack and that they have taken the necessary steps to stop this campaign.
malwarebytes[/caption] Malicious actors registered to various ad platforms posing as legitimate advertisers and submitted their creatives through Real Time Bidding. The companies they were purporting to represent appeared legitimate on the surface, with websites registered years ago with even some listed in the Better Business Bureau registry. This decoy worked well enough to fool many ad networks with direct ties to the major ones in the online ad industry, the researcher stated. “The ads themselves were loaded directly from the rogue advertisers’ websites, which, as we will see it later, was part of the problem in compromising the advertising chain. However it is worth mentioning that the ads themselves were not booby trapped at all, which again made it more difficult to spot something suspicious.” The most notable publishers that were affected include: eBay.co.uk, Answers.com, Legacy.com among others. For this particular malvertising campaign, the techniques used are similar to previous ones, but great care was put on masquerading as legitimate advertisers and avoiding detection by encrypting traffic and using various advanced tricks. Use of URL shorteners, as well as a custom API to perform the redirection to the Exploit Kit landing pages were also noticed. As was the case with past malvertising attacks, the Angler Exploit Kit was used to convert incoming web traffic into infected machines. While malvertising has made headlines during the past few months, the attacks that are documented publicly are only the tip of the iceberg. There are some campaigns that are so advanced that no one will ever see or hear about them, which is exactly what threat actors are hoping for. This particular case is a good illustration of why screening advertisers is so important, especially when they are allowed to host and serve the ad content themselves. The ad could be clean or booby trapped, but the rogue actors are in full control of the delivery platform and can instruct it to perform nefarious actions that will easily bypass most security checks. Malwarebytes said that ad networks have been informed about the attack and that they have taken the necessary steps to stop this campaign.
Malvertising campaign that remained undetected for 3 weeks
FP Staff
• September 15, 2015, 14:54:04 IST
The most notable publishers that were affected include: eBay.co.uk, Answers.com, Legacy.com among others.
Advertisement
)
End of Article