Security News - Page 23

Hackers, IT Units Focusing On Smartphone Security
Mobile phones have become a key target for hackers and an increasing worry for corporate IT departments.

80% Of Mistyped URLs Lead To Typosquatting Sites: Study
Sophos study investigates every possible one-character typo of Facebook, Google, Twitter, Microsoft, Apple and Sophos homepage

Stratfor Hackers Publish Email, Password Data
The hackers had promised that the release of the stolen data would cause "mayhem".

IT Security Year In Review: 2011
James Lyne, Director of Technology Strategy, Sophos, outlines the top trends of 2011 and predictions for key developments in 2012

Stuxnet Has At Least Four Cousins: Research
The platform that was used to build Stuxnet and Duqu was also used to create at least three others, says Kaspersky research.

Hackers Ready To Publish Emails Stolen From Stratfor
The hacking group known as Antisec has claimed responsibility for the attack and promised to cause "mayhem" by releasing stolen documents.

GSM Phones Vulnerable To Hijack Scams: Research
Mobile security is a hot issue because hackers are paying unprecedented attention to the devices as smartphone sales have outpaced sales of PCs.

Hackers Hit Security Think Tank Stratfor's Website
Some of the names of corporate subscribers had been made public, the company says.

HP Services Alleviate Cloud Adoption Security Concerns
Introduces new services that address common security concerns associated with cloud adoption.

Insider Threats Constantly Keeping Banks On Their Toes
Hitesh Mulani, CISO, Yes Bank apprises on the evolving threat landscape in the banking sector and the factors determining the same.

CISOs Should Act As Chief Information Security Selling Officers
In case of an absence of any sort of seriousness from the internal customers, CISOs should conduct a thorough dialogue for putting their point through

Office 365 Now Compliant With EU And US Security Standards
Microsoft announces improvements to its support for security and privacy in Office 365

Safeguard Yourself From Typosquatting This Christmas
We've all made typing mistakes when typing a Web address in our browser. In better cases, we get nothing more than a 404 not found error. In worse cases, we might be redirected to a scam site.

Gartner Survey Shows 18% Of Respondents Are Not PCI-Compliant
PCI data security standards may be a hot topic, but a Gartner survey reveals quite a high percentage of non-compliance to PCI standards.

India Ranks Highest In Flouting IT Regulations At Workplace
Cisco report reveals startling attitudes toward IT policies and growing security threats posed by the next generation of employees entering the workforce

ISACA Issues COBIT Assessment Programme
To help enterprises ensure consistent and reliable processes.

Rigid Compliance Helped India BFSI In The Downturn
"None of the banks in India failed in the light of the economic crisis because of strong regulations by RBI," says Dr. Meera Aranha, Chief Compliance Officer, Karnataka

23% Of IT Pros Have Incorporated Cloud Services Into BC/DR Plans
InformationWeek Reports announces the release of its latest research report - Cloud's Role in BC/DR

UIDAI Will Bring Data Privacy To The Fore
Devendra Parulekar, Partner, Advisory Services, Ernst & Young opines UIDAI will prop up the importance of data privacy among general masses and the Indian enterprise community

Cyber Attacks Could Wreck World Oil Supply
Oil company executives warned that attacks were becoming more frequent and more carefully planned.

Targeted Attacks On The Rise; Spam Down
Symantec announces results of the November 2011 Symantec Intelligence Report.
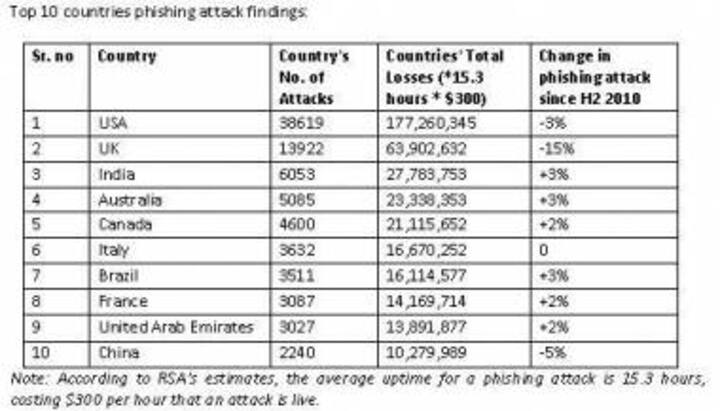
India Inc Lost $27.8 Mn In Phishing Attacks In H1 2011: RSA
RSA has also ranked India as the third most targeted country for phishing attacks after the US and UK.

Sophos Unveils Latest Version Of Endpoint Security Solution
Features integrated patch assessment, comprehensive web protection, filtering and encryption for the new threat environment

ISACA Releases Guidance On Managing Mobile Payments Risks
ISACA has released white paper providing guidance on managing risks associated with mobile payments

Hackers 'Jailbreak' RIM's PlayBook Tablet
Hackers claim exploiting a vulnerability in RIM's PlayBook tablet to gain root access to the device

IT Budgets Moving Out Of The Control of IT Departments
Gartner has announced its top predictions for IT organisations and users for 2012 and beyond

US vulnerable to cyber attacks - military chief
Recent attacks on Google, the Nasdaq stock exchange, Lockheed Martin, and RSA, have given US government a renewed sense of urgency about addressing threats.

2012 Cyber Security Predictions
With all of the crazy 2011 security breaches, exploits and notorious hacks, what can we expect for 2012?

Security Strategy Centered Around Desktop Virtualisation
How Citrix leverages technology and best practices to minimise risk and protect the organisation

Kaspersky Lab, Tech Mahindra, Mahindra Satyam Sign MoU For InfoSec
Solutions to address security threats to consumers and corporates in India and APAC.