Security News - Page 20

McAfee Unveils Situational And Risk Aware SIEM Solution
McAfee Enterprise Security Manager provides intelligence and takes SIEM to a real-time understanding of the global threat landscape.

Vulnerability Volume Down, Not Risk: HP
HP Research identifies new era of security risk, shifting vulnerability landscape.

'Dirty Disks' Raise Questions About Cloud Security
Context Information Security identifies significant flaws in the implementation of cloud infrastructure services offered by some providers.

Worldwide UTM Mkt Surpassed The $1 Billion Mark In 2011
APAC had the strongest growth of any region in 2011, growing 31.8 percent in 2011.

How Cybercriminals Infect Networks And Steal Data Undetected
Websense Security Labs outlines top recommendations and insights for protecting from and containing sophisticated malware and targeted attacks.

Adopt Ethical Hacking As A Security Practice: Frost & Sullivan
Cos should consider the value of ethical hacking services, which are rapidly gaining attention as an essential security practice that should be performed on a regular basis.

Cos Should Incorporate IT Security Into Corporate Governance Framework
New technologies incite new attacks that challenge business enterprises, notes Frost & Sullivan

Data Breaches Cost India Inc. Rs. 53.5 Mn: Symantec
Malicious attacks are the costliest type of data breach in India, says Symantec.

Android Threats Dominate This Quarter's Cybercrime Scene
Trend Micro issues new security roundup report for Q1 2012.

Enterprises Lack Choice Of Endpoint Security Solutions: Ovum
Enterprises do not have a clear and comparable choice of endpoint protection solutions that completely meet today's mobile working security requirements, says Ovum.

Netmagic Gets CERT-In Empanelled For IT Security Auditing
Empanelment empowers Netmagic to carry out IT security audits, including vulnerability assessment and penetration testing.

Structured Approach To Organisational Risk Management
Managing risk for an enterprise has become an important business driver and an act of survival.

Delivering Tomorrow's Backup And Recovery Infrastructure
The next generation of data protection and recovery software functionality continues to evolve.

44% Of Cos Worldwide Plan To Increase IT Investments In 2012: ISACA
ISACA releases COBIT 5, the business framework for the governance and management of enterprise IT.

Wolters Kluwer Helps Banks Meet RBI Guidelines
Wolters Kluwer Financial Services helps banks meet regulatory reporting and compliance requirements in India.

Pitney Bowes India Introduces LobbyTrac: Security Visitor Mgmt System
Solution streamlines the process of visitor management and enables organisations to control access to their facilities.

WatchGuard Positioned In Gartner's Leaders Quadrant For UTM
According to Gartner, the Leaders quadrant contains vendors at the forefront of making and selling UTM products that are built for midsize business requirements.

McAfee Launches MOVE To Secure Virtualised Environments
McAfee's AV solution provides comprehensive defences against physical and virtual attacks.

How To Keep Your Data And Devices Safe On The Move
Tips to avoid having sensitive data stolen or devices infected while travelling.

Sophos Acquires DIALOGS
Together with DIALOGS, Sophos strengthens its mobile footprint, providing complete security for mobile workforces.

New 'Mousetrap Trojan' Steals Your Money By Chain Reaction
New script downloads an applet, that downloads a downloader Trojan, that downloads a banker Trojan, that downloads... pure malice.

SafeNet Unveils White Box Cryptography Software Protection Solution
Solution protects security algorithms from attacks in "white box" environments.

Security Breach Hits U.S. Card Processors, Banks
Payment network operators MasterCard, Visa, American Express and Discover Financial Services confirmed they were affected.

BYOD: Risks And Remedies
The demand to use smart devices in and for the enterprise is rapidly rising. However, IT leaders are still hesitant to cave in with the high risks posed by BYOD phenomenon.

Traditional Risk Mgmt Insufficiently Agile To Deal With Complex Threats
Information Security Forum provides organisations with insights into managing risks as security threats collide.

Embed Security In The Source Code
Michele Orru', Penetration Testing Specialist, Royal Bank of Scotland Group, in conversation with Revathi Raghavan, suggests developers should be taught the importance of secure code.

Collaborative Business Environment Needs Sound Risk Mgmt
How do you ensure the same rigour for security compliance when you have so many stakeholders that may not directly, or even indirectly, be in your sphere of influence?
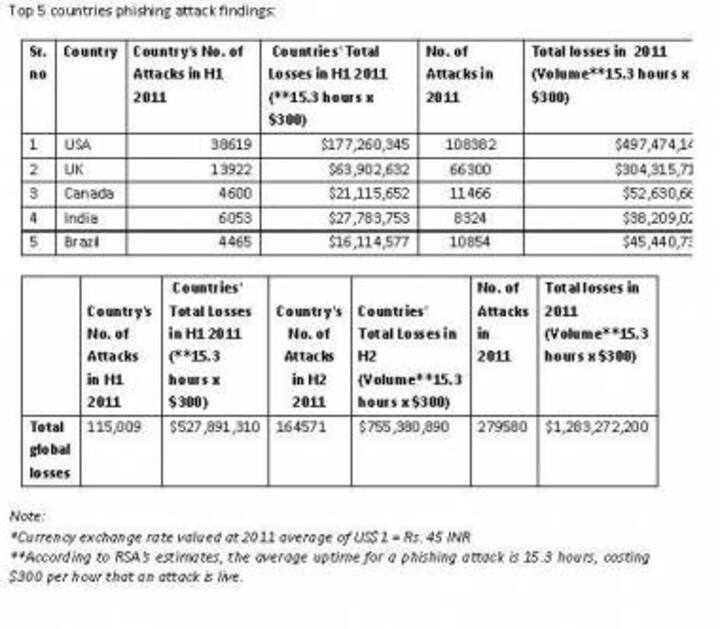
India Inc Loses Rs.171.94 Crore From Phishing Attacks In 2011
RSA has ranked India in the top five most targeted countries for phishing attacks.

Ciena, SafeNet Ally For Data Protection In Commercial, Govt Networks
Companies to jointly sell high-speed, low-latency Ethernet link encryption solutions specifically designed to work at Layer 2.

M&As Surge With Need For More Network Security
The demand for more sophisticated protection makes niche network security firms prime takeover targets.