Security News - Page 10

35% Of Businesses Have Lost Data Due To Flawed IT Security
25 percent of IT specialists cite vulnerabilities in installed applications as the most common internal cause of data loss.

Changing Security Threat Vectors In The Datacentre
Sajan Paul, Director-Systems Engineer, India & SAARC, Juniper Networks talks about security in the new age datacentres and the dealing with the phenomenon of ‘cloud+mobile 'clobile'.’

Symantec Puts Altiris Unit Up For Sale: Reports
The sale is expected to fetch less than the amount Altiris was bought for, the daily said.

CA Technologies Offers Unlimited Data Protection For Three Years
From now until March 31, 2013, customers choosing CA ARCserve can purchase an unlimited-use Managed Capacity license for their business for the next three years.

Kaspersky Lab Identifies Cyber-Espionage Campaign "Red October"
Campaign has been targeting diplomatic, governmental and scientific research organisations in several countries.

CISOs Move "Internet Of Things" From Incidental To Important
IDC highlights top 10 predictions for Chief Information Security Officer in 2013.

U.S. Says Java Still Risky, Even After Security Update
"Unless it is absolutely necessary to run Java in web browsers, disable it," the Department of Homeland Security's Computer Emergency Readiness Team said.

Oracle Updates Java, Security Experts Say Bugs Remain
Oracle said on its security blog that its update fixed two vulnerabilities in the version of Java 7 for Web browsers.

U.S. Warns On Java Software As Security Concerns Escalate
The U.S. Department of Homeland Security urged computer users to disable Oracle Corp's Java software, amplifying security experts' prior warnings.

Security Chiefs Pitch Actionable Strategies To Survive 2013
RSA recommendations outline how security teams can reduce risk through rapid innovation.

Corporate India Not Equipped To Deal With Futuristic Fraud: KPMG
Corporate India's unwillingness to see fraud as a strategic risk poses a grave threat to firms as they start experiencing frauds of the future, indicates the KPMG India Fraud Survey 2012.

Windows Is The Most Attacked OS: Report
The Windows operating system, because of its popularity and widespread use, is still a highly targeted platform.

99% Of All Mobile Threats Target Android Devices
From a negligible eight new unique malicious programs in January 2011, the average monthly discovery rate for new Android malware in 2011 went up to more than 800 samples.

Sophos Leads Endpoint Protection Platforms In 2013 Magic Quadrant
Sophos was also positioned as a "Leader" in the 2012 Magic Quadrant for Mobile Data Protection and the 2012 Magic Quadrant for Unified Threat Management.

Essar Group Implements Sanovi DRM For Recovery Readiness
Solution helps overcome lack of real-time monitoring of DR Readiness, incident management, application-level replication of processes as well as database.

Mobile Apps The Easiest Way To Compromise Devices: Report
Quick Heal Technologies Pvt. Ltd. has released the findings from its Mobile Malware report, showing that mobile device malware has reached a new stage of evolution.

2013 Will See CISOs Arrive At A Balanced BYOD Policy: IDC
This year, IDC predicts CISOs will arrive at a BYOD security policy that strikes a balance between user freedom and protection of corporate assets.
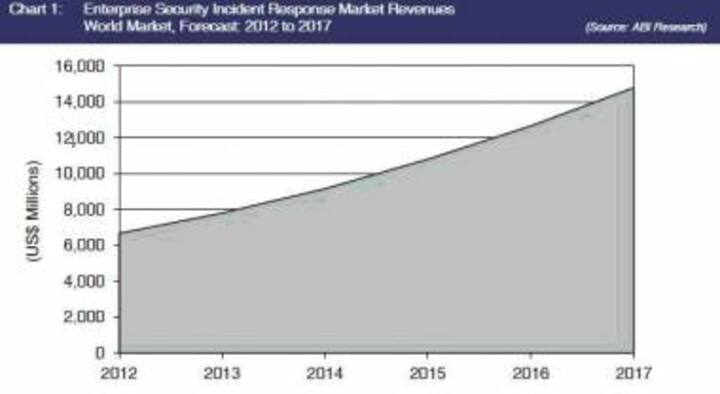
Enterprise Incident Response Mkt Booms To $14 Bn As Threats Multiply
Incident response solutions are increasingly moving from a reactive to a pre-emptive model, finds ABI Research.

Security Appliance Mkt Growth Continues To Slow In 3Q12: IDC
While the security market remains more resilient than others, there was a definite slow-down in growth rates, finds IDC.

Antivirus Solutions Woefully Inadequate: Study
Antivirus solutions in study unable to detect newly created viruses; security investment misaligned.

APT Targets The Little Guy
Smaller businesses continue to face cybercrime threats in 2013, finds Imperva study.

MDM, DLP To Bite Into Major Chunk Of 2013 Security Budgets
2013 will be a key year for mobile device management implementations, finds TheInfoPro study.

India Third Most Targeted Country By Phishing: Report
India endured 7 percent of phishing attack volume last month.

ISACA Issues Guidance On Managing Biz Challenges In 2013
ISACA survey finds that the most effective way to reduce IT risk is to educate employees.

Iran Thwarts US Cyber Attack: Report
According to the Fars news agency, the cyber attack targeted the culture ministry institutes and it was repelled by the experts.

McAfee's Top 10 Threat Predictions For 2013
2013 will see significantly more targeted attacks and targeted malware, predicts McAfee.

CIO Guidelines On IT Governance
While the IT governance practice has been around for long, what's really bringing its role into prominence is the IT and business alignment reality.

EWI Releases Report On 3rd Worldwide Cybersecurity Summit In New Delhi
The report contains results of an informal poll of participants, where 93 percent expressed the view that the cybersecurity risk is higher than one year ago.

IT Security In 2030: Kaspersky
Magnus Kalkuhl, Director of Kaspersky Lab's European Global Research and Analysis Team, predicts the future of IT will dramatically shift by 2030.

Data Breaches Get Personal: Symantec Intelligence Report, 2012
What may seem surprising is that a person's real name is by far the most common item to be stolen in a data breach, where it is obtained 55 percent of the time.